Recently I’ve been implementing Sopho XGS firewalls at clients’ sites. The one thing I was concerned about was setting up 3CX with these firewalls, as 3CX can be notoriously picky. Luckily with the new XGS the setup was mostly painless. I did have a few small issues but they were easily fixed.
- First log into your firewall and go to System -> Hosts and services. Select add an IP host. Enter the name and the IP of your 3CX server.

- Next go to the Services tab and select add. We are going to add all the required 3cx services and ports to one group for easy management. You don’t want to change the source ports as this is where the traffic is coming from. (My web port is 1443 but change if yours is different) Select save.

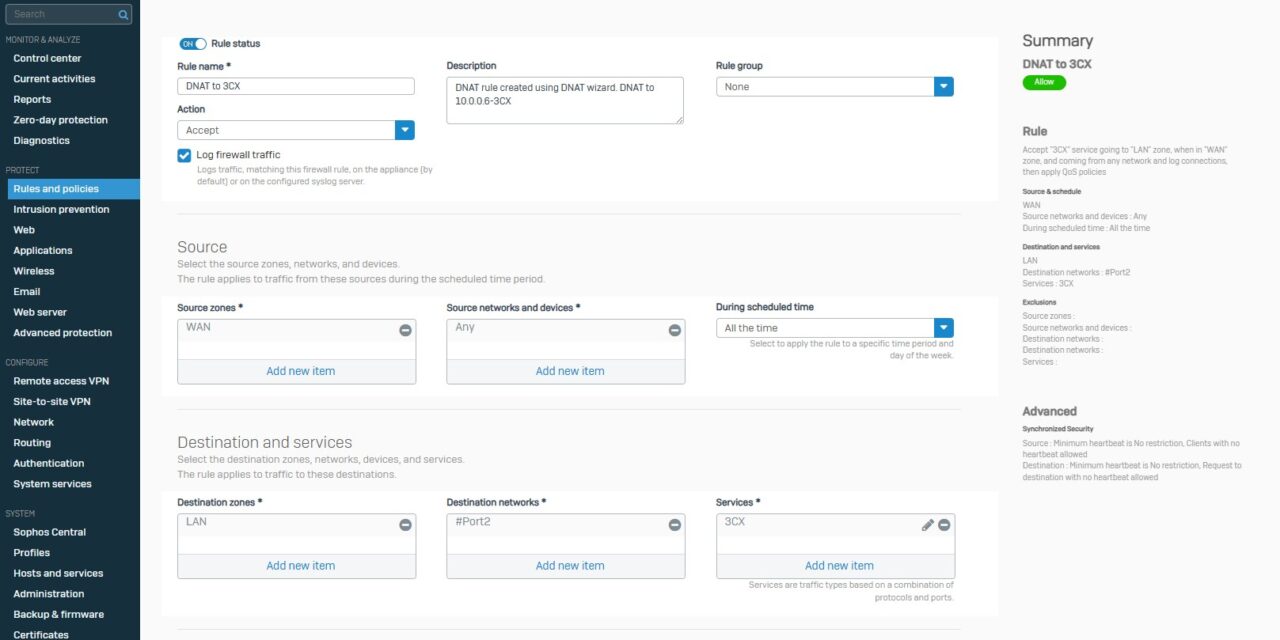
- Now go to Protect -> rules and policies. Under Firewall rules we will add one to allow the incoming connections from the WAN. Select add firewall rule. Give the rule a name, description and select log traffic. For the SOURCE select the source zone as WAN, for the source network leave as Any. For the DESTINATION select the zone where the 3CX server is, for my testing it is LAN, for the Destination network select your WAN Physical port (#Port2 by default). For the services select the 3CX group we created earlier. The only other option I changed was Shape Traffic to VOIP Guarantee.

- Now head to NAT rules. Here we will direct the traffic from the WAN to the 3CX server. Select add NAT rule. For the original source leave as Any, for original destination select #Port2, for original service select the 3CX group we created earlier, for translated destination select the 3CX server, for inbound interface select your WAN interface (Port2) and leave outbound interface as Any.

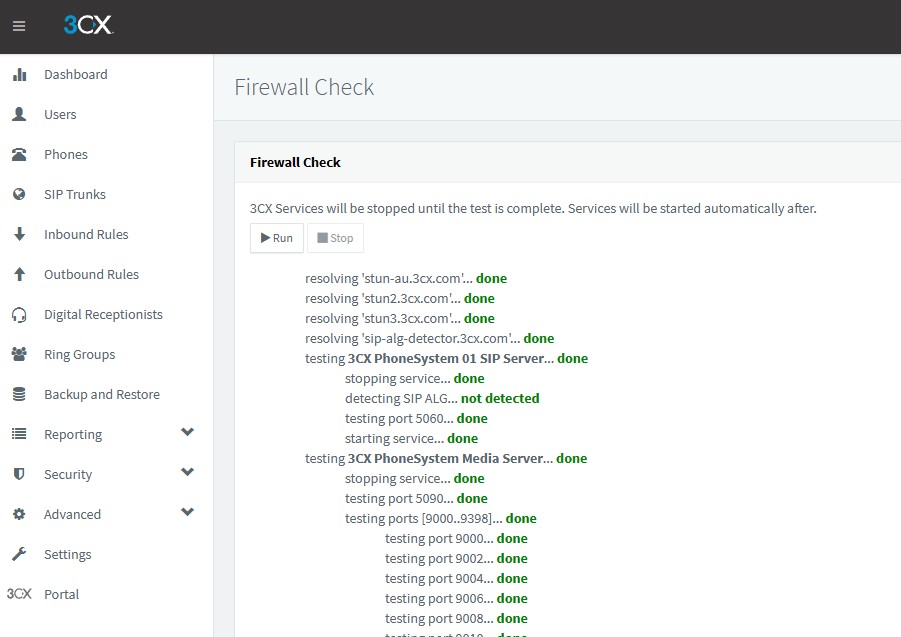
- With those rules set up you should be able to run a 3CX firewall test and it should all show as green.




Thanks for the tutorial! Just a quick tip for those with multiple WAN connections:
To ensure all 3CX traffic uses a specific WAN interface, go to Routing > SD-WAN Routes and create a route as follows:
1. Source Network: Set this to the IP address of your 3CX server (though it says “source networks,” you can specify an individual host).
2. Leave everything else as Any, but set Link Selection to use Primary and Backup Gateways. Choose your preferred gateway and enable Route only through specified gateways.
I initially tried using static routes to the VoIP provider, but the 3CX Firewall Checker failed because the test traffic originates from a different IP address. I also attempted SD-WAN routing with 3CX services, but that consistently led to a Full Cone NAT Failure in the 3CX Firewall Checker.