Recently I’ve been testing WireGuard with my PFSense setups, rather than IPsec and OpenVPN. I’ve found it really good and I think WireGuard works really well. The one thing I was a little stuck on was how to allow remote clients from one site to access devices on the second sites LAN.
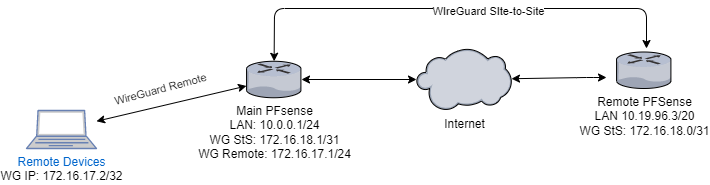
| Main Site | Remote Site | |
| LAN | 10.0.0.1/24 | 10.19.96.3/20 |
| WireGuard Site to site | 172.16.18.1/31 | 172.16.18.0/31 |
| WireGuard Remote Clients VPN | 172.16.17.1/24 |
I want my remote devices connected to the main site via the WireGuard to be able to access the 10.19.96.3/20 LAN on the remote site.
Assumptions
- You already have a WireGuard Site-to-Site VPN setup and can route traffic between the two sites LAN’s.
- You already have a wireGuard remote client VPN setup and can access the main sites LAN
Simple Fix
- Log into your Remote PFsense router. Go to System -> Routing -> Static Routes.
- Add a static route for your WireGuard Remote Clients VPN subnet(Main Site), use the WireGuard Site-to-Site VPN Gateway.

- Now go to VPN -> WireGuard-> Peers. Select edit on your main site peer.
- Under the Address Configuration, add your WireGuard Remote Clients VPN subnet(Main Site) to the allowed IP’s.

- Now remote clients connected to the main site should be able to access your remote sites LAN.



bit off more than i can chew… installed on 2 sites pfsense with synology nas behind them, now can’t access the DSMs from outside the firewall, and not sure how to link/create the site-to-site wireguard…
would you be able to point to some of your walkthroughs/guides anywhere? seems most of the tutorials out there are for openvpn set ups for pfsense-synology so not easy to get to the bottom of this…
thank you
Hi Ewo,
I’m not exactly sure what your trying to do, the Synology Nas will act like any other device behind the firewall.
I don’t have a guide on setting up a wireguard site to site VPN but I would recommend following the netgate guide.
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-s2s.html
thank you for the reply… what I am trying to do is that after upgrading from Asus routers to pfsense, now i am told i should not open ports (as not secure) and instead use wireguard/openvpn to access the NASs (as well as back up between the NASs).
problem is now I can’t
1) access the NAS GUI using the somain.synology.me:5001 route?
2) the DSM client on laptop can’t sync with the NAS anymore as there is now no port forwarding?
How does one use pfsense VPN to achieve both above without opening ports, or is port opening really the only effective and not overkill way to manage the synology boxes?
Hi Ewo,
Opening the port really is the easiest way to connect to the synology. Just make sure that you have a strong password and set up 2 factor authentication.
If you use a vpn to connect to the network, you would need to use the internal IP of the synology to connect to it. Otherwise you would have to setup DNS overrides in pfSense ie somain.synology.me points to the internal IP of your synology. Then when using the VPN you need to set the DNS server as your pfSense router.
From my remote device (wg vpn) i cant connect to a device on the Remote pfSense (in a site to site WG setup).
i have all the firewall rules open, and my wg config includes: AllowedIPs = 0.0.0.0/0
However i cant connect. However when i use OpenVPN on the remote device i can connect. So im assuming it would be an issue with my wg config on the remote device i.e. my laptop? What am i missing here?
Hey John,
Have you definitely followed my steps above? They are addressing that exact issue.
Thanks, that was exactly the missing piece I was looking for all day! Thanks for sharing this!
Hey Florian,
Thats great, glad I could help!